Dan Goodin
Google’s risk assessment group, which counters focused and govt-backed hacking against the enterprise and its customers, despatched account holders pretty much 40,000 warnings in 2019, with federal government officials, journalists, dissidents, and geopolitical rivals getting the most targeted, team members claimed on Thursday.
The variety of warnings declined virtually 25 percent from 2018, in component since of new protections designed to suppress cyberattacks on Google qualities. Attackers have responded by lowering the frequency of their hack tries and being far more deliberate. The group noticed an boost in phishing assaults that impersonated news outlets and journalists. In quite a few of these conditions, attackers sought to distribute disinformation by trying to seed false stories with other reporters. Other situations, attackers despatched quite a few benign messages in hopes of developing a rapport with a journalist or international plan professional. The attackers, who most regularly arrived from Iran and North Korea, would afterwards observe up with an e-mail that provided a destructive attachment.
“Government-backed attackers regularly target foreign plan professionals for their investigation, accessibility to the corporations they get the job done with, and link to fellow researchers or policymakers for subsequent assaults,” Toni Gidwani, a stability engineering manager in the threat examination team, wrote in a post.
Best targets
Countries with inhabitants that collectively gained extra than 1,000 warnings integrated the United States, India, Pakistan, Japan, and South Korea. Thursday’s write-up arrived eight months following Microsoft reported it experienced warned 10,000 buyers of country-sponsored assaults over the 12 previous months. The software program maker said it noticed “extensive” exercise from 5 distinct teams sponsored by Iran, North Korea, and Russia.
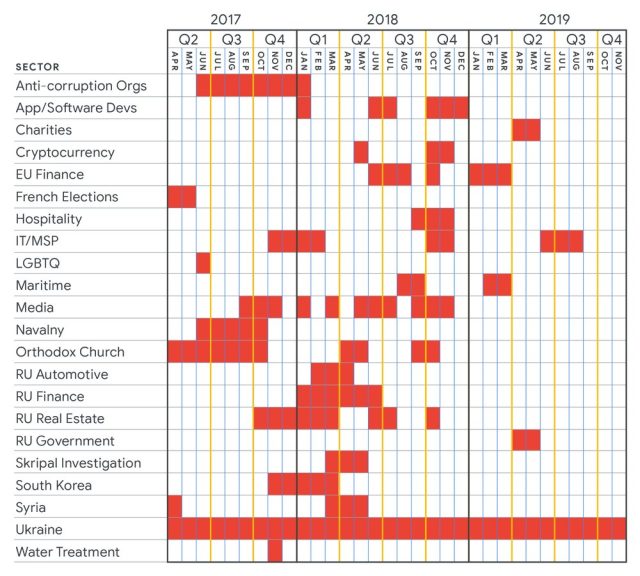
Thursday’s submit also tracked qualified assaults carried out by Sandworm, thought to be an assault team functioning on behalf of the Russian Federation. Sandworm has been dependable for some of the world’s most critical assaults, like hacks on Ukrainian electrical power amenities that still left the nation without the need of energy in 2015 and 2016, NATO and the governments of Ukraine and Poland in 2014, and according to Wired journalist Andy Greenberg, the NotPetya malware that designed all over the world outages, some that lasted weeks.
The next graph exhibits Sandworm’s targeting of various industries and countries from 2017 to 2019. Although the targeting of most of the industries or countries was sporadic, Ukraine was on the obtaining conclude of assaults all over the total a few-calendar year period:
Tracking zero-times
In 2019, the Google group learned zero-working day vulnerabilities influencing Android, iOS, Windows, Chrome, and Web Explorer. A single assault team was dependable for exploiting 5 of the unpatched stability flaws. The attacks were being used against Google, Google account holders, and customers of other platforms.
“Finding this many zeroday exploits from the exact same actor in a comparatively brief time body is unusual,” Gidwani wrote.
The exploits came from authentic internet websites that experienced been hacked, links to destructive web-sites, and attachments embedded in spear-phishing email messages. Most of the targets ended up in North Korea or have been in opposition to folks doing work on North Korea-similar difficulties.
The group’s coverage is to privately advise builders of the afflicted application and give them seven times to launch a repair or publish an advisory. If the companies really don’t meet that deadline, Google releases its personal advisory.
A single observation that Google customers really should be aware: of all the phishing assaults the corporation has viewed in the earlier several many years, none has resulted in a takeover of accounts shielded by the account safety software, which amongst other issues can make multifactor authentication obligatory. When people today have two bodily protection keys from Yubi or an additional manufacturer, enrolling in the plan normally takes less than five minutes.




