Dan Goodin
Researchers have unearthed an attack marketing campaign that uses formerly unseen malware to goal Middle Jap organizations, some of which are in the industrial sector.
Scientists with Kaspersky Lab, the protection firm that found out the campaign, have dubbed it WildPressure. It takes advantage of a relatives of malware that has no similarities to any malicious code seen in previous attacks. It is really also concentrating on companies that don’t overlap with other regarded campaigns.
Milum, as the malware is dubbed, is written in C++ and includes clues that advise builders may be doing the job on variations created in other programming languages. Though Milum utilizes configuration details and communication mechanisms that are prevalent among malware builders, the researchers believe that equally the malware and the targets are special.
Awareness finding
“A campaign that is, seemingly, solely concentrating on entities in the Middle East (at the very least some of them are industrial-relevant) is anything that routinely appeals to the attention of any analyst,” Kaspersky researcher Denis Legezo wrote in a write-up revealed on Tuesday. “Any similarities should be regarded as weak in terms of attribution and may simply be procedures copied from previous effectively-known situations. In truth, this ‘learning from more skilled attackers’ cycle has been adopted by some appealing new actors in latest several years.”
Milum samples demonstrate a compilation date of March 2019, a time body that’s dependable with the first identified infection on May perhaps 31, 2019. Kaspersky initially noticed Milum previous August.
The malware utilizes the RC4 encryption cipher with a various 64-little bit important for every single goal. It also employs the JSON structure for configuration details and to connect with handle servers as a result of HTTP POSTs. Fields inside the JSON knowledge correspond to the C++ language and the .exe file extension. That clue led researchers to hypothesize that malware variations based mostly on other languages are in the works or maybe previously exist. To date, the researchers have collected three pretty much equivalent samples, all from the similar undisclosed place.
The malicious application exists as an invisible toolbar window. The malware implements capabilities in a separate menace. Scientists have been unable to entry commands from command servers, but by analyzing command handlers in the malware, the researchers were able to piece together the next:
| Code | Which means | Functions |
| 1 | Execution | Silently execute received interpreter command and return result by means of pipe |
| 2 | Server to shopper | Decode obtained articles in “data” JSON field and fall to file outlined in “path” discipline |
| 3 | Customer to server | Encode file talked about in received command “path” area to deliver it |
| 4 | File data | Get file attributes: hidden, read only, archive, method or executable |
| 5 | Cleanup | Make and operate batch script to delete itself |
| 6 | Command end result | Get command execution position |
| 7 | Method data | Validate goal with Home windows variation, architecture (32- or 64-little bit), host and person identify, mounted security items (with WQL request “Select From AntiVirusProduct Wherever displayName “Windows Defender”) |
| 8 | Listing listing | Get information about files in directory: hidden, read through only, archive, system or executable |
| 9 | Update | Get the new model and remove the previous 1 |
When scientists took management of 1 of the campaign’s management servers, they noticed generally desktops situated in the Center East connecting. (The researchers believe that the IP addresses not located in the Middle East belonged to network scanners, Tor Exit nodes, and VPN connections.) Some of people Middle Jap IP addresses belonged to businesses occupying the industrial sectors. Milum will get its name from a string located in one particular of the executable file names, as very well as C++ course names inside of the malware.
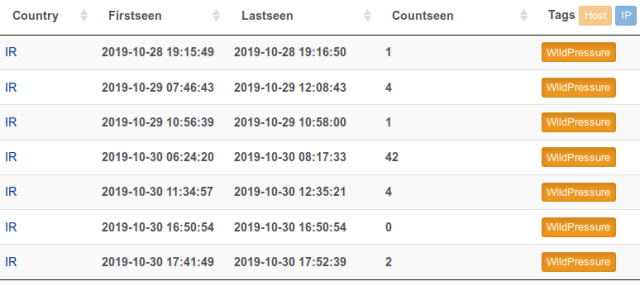
Kaspersky Lab
The previously mentioned screenshot of a Kaspersky laptop or computer connecting to the sinkholed manage server confirmed only gadgets centered in Iran connecting. Tuesday’s write-up did not establish the nations around the world of other contaminated companies.
Above the earlier ten years, the Center East has emerged as a hotspot for hacking operations, with (to title only 4) an attack targeting security controls in vital infrastructure facilities, a reportedly US procedure that hobbled Iran’s capability to goal oil tankers, a damaging disk-wiping campaign towards a Saudi Arabian gasoline firm, and the Stuxnet and Flame malware that specific Iran. The discovery of WildPressure and Milum suggest assaults in the location are not possible to die down any time quickly.




