Dan Goodin
A not long ago learned hack of property and tiny-office routers is redirecting end users to malicious web pages that pose as COVID-19 informational assets in an endeavor to put in malware that steals passwords and cryptocurrency qualifications, researchers said on Wednesday.
A write-up posted by stability company Bitdefender explained the compromises are hitting Linksys routers, although BleepingComputer, which claimed the attack two days back, said the marketing campaign also targets D-Hyperlink units.
It continues to be unclear how attackers are compromising the routers. The scientists, citing info collected from Bitdefender stability products and solutions, suspect that the hackers are guessing passwords applied to safe routers’ remote administration console when that characteristic is turned on. Bitdefender also hypothesized that compromises may well be carried out by guessing qualifications for users’ Linksys cloud accounts.
Not the AWS site you are on the lookout for
The router compromises let attackers to designate the DNS servers linked units use. DNS servers use the World wide web area title process to translate domain names into IP addresses so that personal computers can obtain the area of web sites or servers consumers are making an attempt to entry. By sending products to DNS servers that deliver fraudulent lookups, attackers can redirect folks to malicious sites that provide malware or endeavor to phish passwords.
The destructive DNS servers mail targets to the domain they requested. Powering the scenes, on the other hand, the web-sites are spoofed, which means they are served from destructive IP addresses, alternatively than the legit IP address used by the domain owner. Liviu Arsene, the Bitdefender researcher who wrote Wednesday’s post, advised me that spoofed websites close port 443, the World wide web gate that transmits traffic shielded by HTTPS authentication protections. The closure triggers websites to connect around HTTP and in so accomplishing, helps prevent the screen of warnings from browsers or email consumers that a TLS certification is invalid or untrusted.
Domains swept into the campaign contain:
- aws.amazon.com
- goo.gl
- little bit.ly
- washington.edu
- imageshack.us
- ufl.edu
- disney.com
- cox.net
- xhamster.com
- pubads.g.doubleclick.net
- tidd.ly
- redditblog.com
- fiddler2.com
- winimage.com
The IP addresses serving the destructive DNS lookups are 109.234.35.230 and 94.103.82.249.
The malicious-web-sites people land on assert to give an app that presents “the hottest facts and guidelines about coronavirus (COVID-19).”
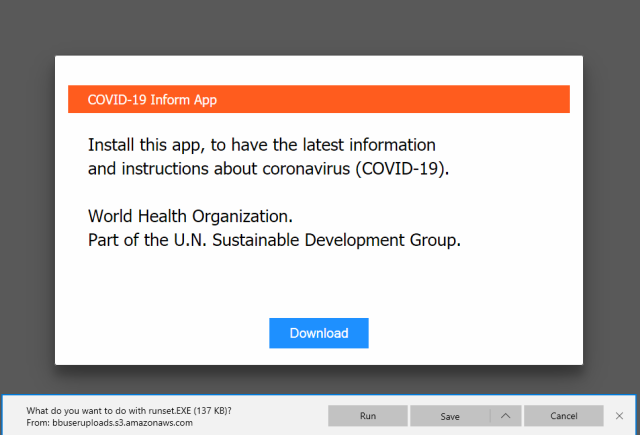
Bifdefender
Customers who simply click on the download button are eventually redirected to a person of numerous Bitbucket webpages that gives a file that installs malware. Recognised as Oski, the reasonably new piece of malware extracts browser qualifications, cryptocurrency wallet addresses, and quite possibly other varieties of delicate facts.
US, Germany, and France most specific
There had been 1,193 downloads from just one of the 4 Bitbucket accounts applied. With attackers applying at least three other Bitbucket accounts, the down load quantity is possible significantly greater. (The actual quantity of men and women contaminated is possibly smaller sized than the down load overall, due to the fact some people may possibly not have clicked on the installer or accessed the web page for research functions).
Bitdefender details displays the attack started off on or all-around March 18 and strike a peak on March 23. Bitdefender info also demonstrates that the routers targeted the most were being positioned in Germany, France, and the United States. At this moment, these nations are amongst individuals most suffering the devastating results of COVID-19, which at the time this post went are living had caused additional than 436,856 bacterial infections and 19,549 deaths around the globe.
To prevent attacks on routers, the products really should have remote administration turned off any time feasible. In the event this attribute is certainly required, it ought to be made use of only by seasoned people and shielded by a strong password. Cloud accounts—which also make it doable to remotely administer routers—should comply with the similar guidelines. What’s more, men and women really should commonly make sure that router firmware is up-to-date.
People who want to verify if they have been specific can examine the Bitdefender post for indicators of compromise. Choose be aware: the indicators may be tricky for significantly less professional people to comply with.




